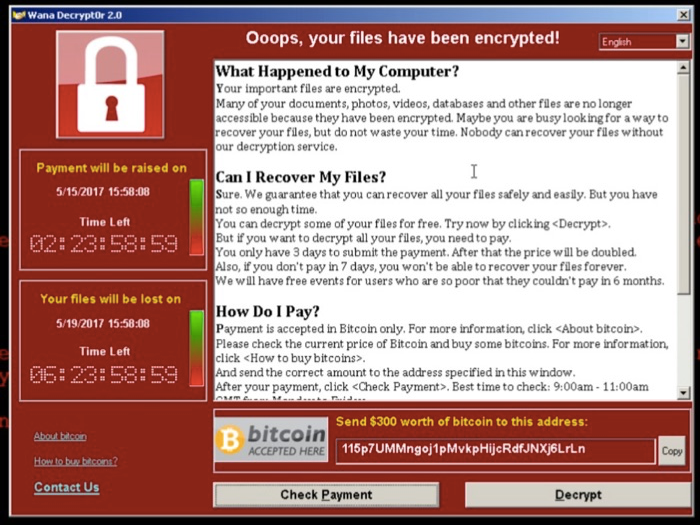

A decade ago, if a dekstop computer got infected with malware the main symptom probably was an intrusive browser toolbar of some kind. These days if your mobile or desktop computer is infected what gets installed is likely to be “ransomware” — malicious software that locks your most prized documents, songs and pictures with strong encryption and then requires you to pay for a key to unlock the files.
What is ransomware?
Ransomware — malicious software that encrypts the victim’s files and holds them hostage unless and until the victim pays a ransom in Bitcoin — has emerged as a potent and increasingly common threat online. But many Internet users are unaware that ransomware also can just as easily seize control over files stored on cloud services.
The role of bitcoin
Since 2013, when Bitcoin first entered the mainstream, it has been used as a payment option for ransomware. While Bitcoin has proven popular for this purpose, the unique properties of the cryptocurrency cut both ways — creating a double-edged sword for attackers.
Irreversible transactions are useful for cybercriminals as they can avoid chargebacks after they have delivered the decryption key. Or they can simply keep demanding more funds without ever delivering.For the attackers, it’s this quality that makes Bitcoin an attractive ransomware payment method. Bitcoin payments cannot be reversed or stopped, unlike wire transfers, prepaid cards, or SMS payments, which in some cases promise higher levels of anonymity.
Attack on the rise
Yesterday, some residents of Johannesburg, the largest city in South Africa, were left without electricity after the city’s power company got attacked by a ransomware virus. City Power, the company responsible for powering South Africa’s financial capital Johannesburg, confirmed Thursday on Twitter that it had been hit by a Ransomware virus that had encrypted all of its databases, applications, and network. The attack prevented prepaid customers from buying electricity units, upload invoices when making payments, or access the City Power’s official website, eventually leaving them without power.
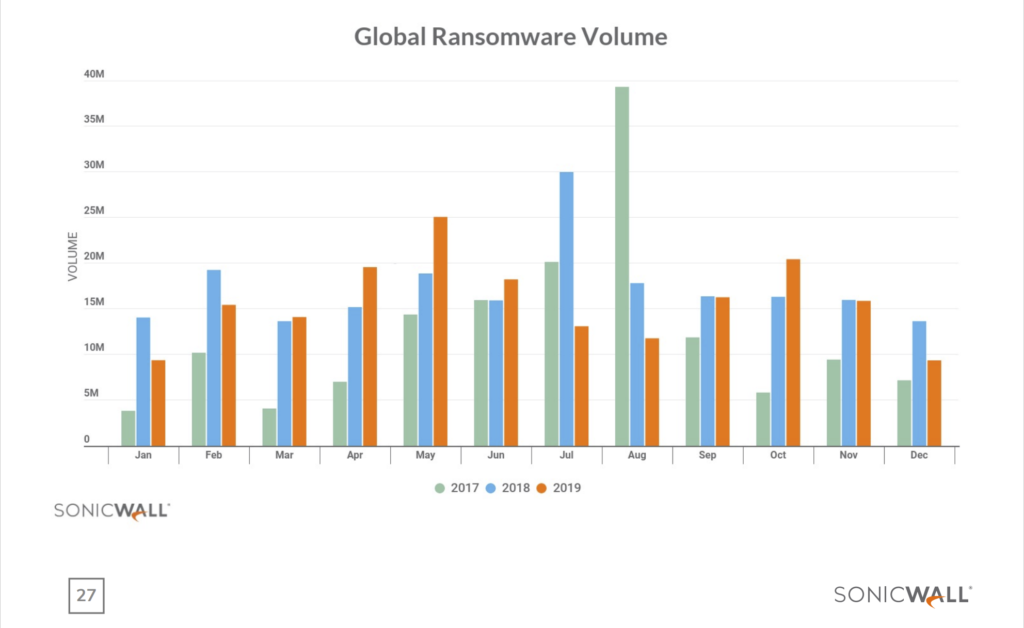
According to SonicWall cyber threat report current trend sees global common malware volume slow down comparing to 2018 and its gets replacing by ransomware attacks which now at the all time high volume hit. In 2018, SonicWall logged more than 2.8 million ransomware malware attacks, which was already a 27% jump over the previous year. So far in 2019, that threat is only accelerating. Through the first six months of 2019, SonicWall has registered 2.4 million ransomware attacks, almost eclipsing the 2018 full-year total in half the time. This marks a 76% year-to-date increase.

How to protect yourself?
Regularly backup your data, and make sure the backups are not connected to the computers and networks they are backing up.Most ransomware variants can encrypt files on any attached drives or network files that are also accessible to the host machine (including cloud hosting and cloud-based backups if those passwords are stored on the machine).
Many companies are now selling products that claim to block ransomware attacks. Those claims are beyond the scope of this article, but don’t be lulled into thinking these products will always protect you.
Even products that could somehow block all ransomware attacks can’t prevent the biggest reason that ransomware attacks succeed: They trick victims into taking an action that inadvertently undermines the security of their device — be it a smart phone, tablet or desktop computer.
This usually involves clicking a link or downloading and opening a file that arrives in an email or instant message. In either case, it is an action that opens the door to the attacker to download and install malware.
With global ransomware projected to generate global revenues of at least a billion dollars this year, ransomware authors are going to keep targeting businesses for the foreseeable future. It is therefore imperative for businesses and endusers to implement available safeguards, create regular data backups and educate employees on how best to avoid triggering a ransomware infection.
