Customers of Ledger, the hardware cryptocurrency wallet, are being targeted by a phishing attack posing as an email from Ledger support. Even we at Bitstore Malaysia also getting this attempt on daily basis.
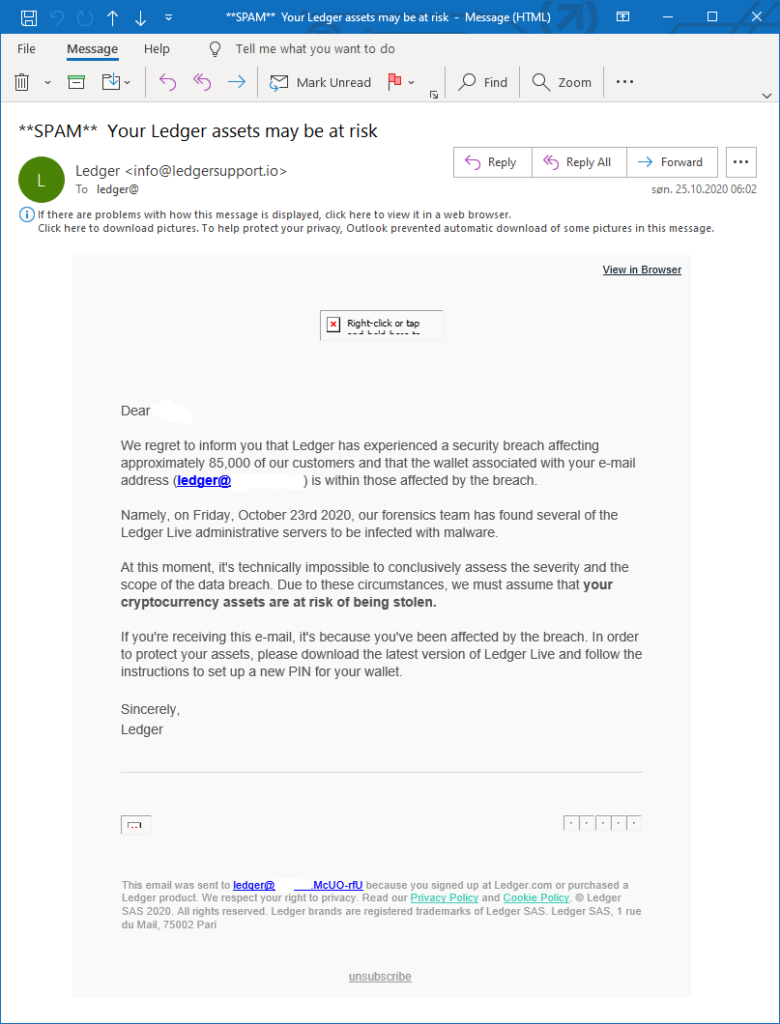
The fake email ostensibly informs users their Ledger assets may be compromised or Your Hardware Wallet has been disabled as head subject. It states, “We‘re sorry to inform you that due to the new KYC (Know Your Customer) regulations, you‘re required verify your identity:.” This claim is false; while the email form looks professional, it is a phishing attempt to steal customers data.
Based on analyst from our threat intelligence team, the email contain a link that will phish user to giving their recovery phrase on the cloud document provided or a link to download fake Ledger Live application.
Security best practices
- Reminder: Anyone with access to your 24-word recovery phrase can take your assets.
- Never enter your 24-word recovery phrase anywhere else than on your Ledger device.
- Ledger will never ask you for your 24-word recovery phrase.
- Only use official contact form at ledger.com/support.
The email is so convincing that even wary users might be fooled. Ledger confirmed that, for the last week, a phishing attack has been targeting Ledger cryptocurrency wallet customers.
In a statement, a Ledger spokesperson said an internal task force has been deployed to investigate the latest phishing attack.
“The investigation is ongoing and at this time we cannot give any additional information but one thing is for certain: Ledger will never ask you for your 24-word recovery phrase, which is a blatant sign of a phishing scam,” said the spokesperson. “Ledger encourages customers to exercise caution as phishing attacks become more sophisticated and to alert Ledger’s customer support team and consult Ledger.com for more information on the detection of scams.”
Phishing attacks are common and attackers are increasingly sophisticated, creating emails that resemble official company correspondence. They rely on a person making a mistake and clicking on a link that could compromise his or her security.
Pro tip: Bookmark verified sites where you normally would input sensitive information and only access them through that bookmarked link.

