Technology has changed the way people work, communicate, shop and even pay for goods. Companies and consumers don’t always prefer cash anymore, and this behavior is giving way to contactless payments. With the quick wave of a smartphone, consumers can pay for items at digital registers. Now, a new payment system is emerging: cryptocurrency.
Probably everyone heard about Bitcoin by now. It was the first cryptocurrency to go mainstream, but others are growing in popularity. There are more than 2,000 different types of cryptocurrencies, and more are developed every day.
Research suggests most people have heard of cryptocurrency but don’t fully understand what it is. So, what is it, is it secure and how do you invest in it? To help, we’ll answer those questions. Think of this as Cryptocurrency Investing 101.
What Is Cryptocurrency?
Cryptocurrency is a digital payment system that doesn’t rely on banks to verify transactions. It’s a peer-to-peer system that can enable anyone anywhere to send and receive payments. Instead of being physical money that is carried around and exchanged in the real world, cryptocurrency payments exist purely as digital entries to an online database that describe specific transactions. When you transfer cryptocurrency funds, the transactions are recorded in a public ledger. You store your cryptocurrency in a digital wallet.
Cryptocurrency got its name because it uses encryption to verify transactions. This means advanced coding is involved in storing and transmitting cryptocurrency data between wallets and to public ledgers. The aim of the encryption is to provide security and safety.
How Secure Is Cryptocurrency?
Cryptocurrencies are usually built using blockchain technology. Blockchain describes the way transactions are recorded into “blocks” and time stamped. It’s a fairly complex, technical process, but the result is a digital ledger of cryptocurrency transactions that’s hard for hackers to tamper with.
In addition, transactions require a two-factor authentication process. For instance, you might be asked to enter a username and password to start a transaction. Then, you might have to enter an authentication code that’s sent via text to your personal cell phone.
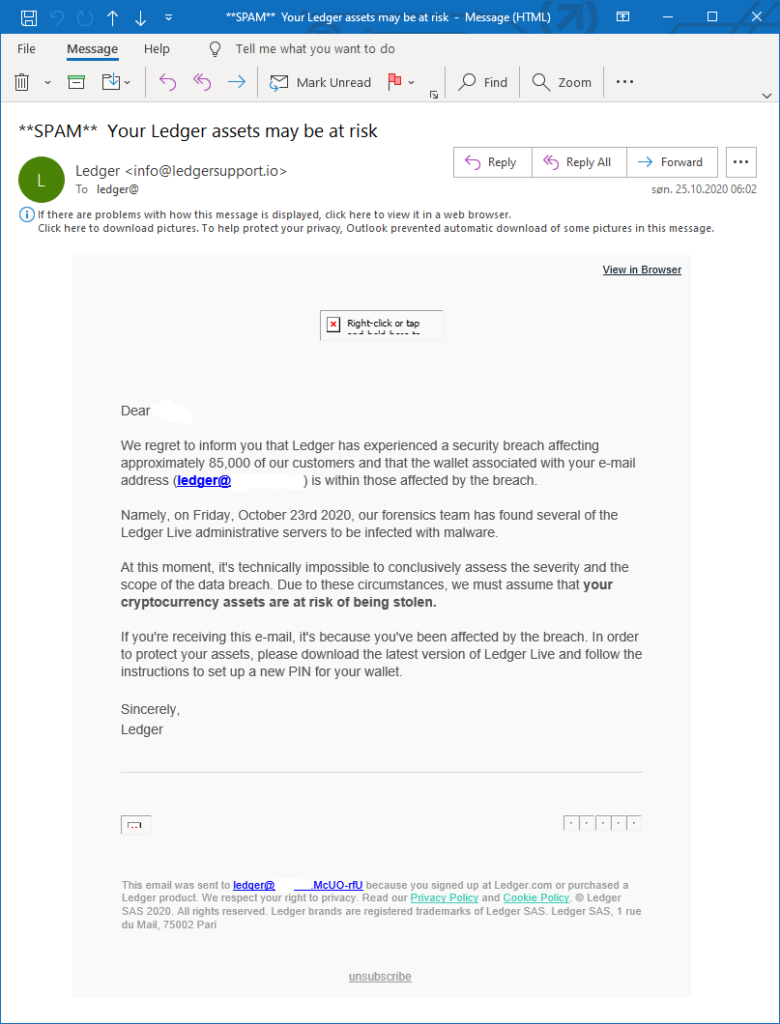
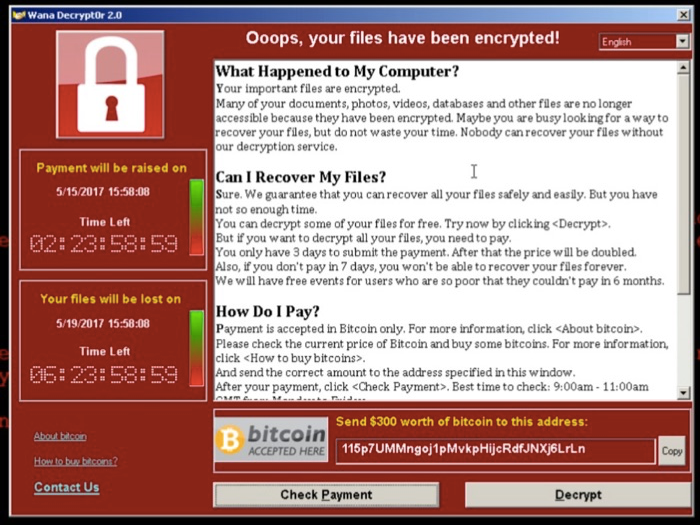
While securities are in place, that doesn’t mean cryptocurrencies are un-hackable. In fact, several high-dollar hacks have cost cryptocurrency startups heavily.
Tips to Invest in Cryptocurrency Safely
Investments are always risky, but some experts say cryptocurrency is one of the riskier investment choices out there, according to Consumer Reports. However, digital currencies are also some of the hottest commodities. If you’re planning to invest in cryptocurrencies, these tips can help you make educated choices.
Research Exchanges
Before you invest one dollar, learn about cryptocurrency exchanges. These platforms provide the means to buy and sell digital currencies, but there are thousands exchanges to choose from. Do your research, read reviews and talk with more experienced investors before moving forward.
Know How to Store Your Digital Currency
If you buy cryptocurrency, you have to store it. You can store it on an exchange or in a digital “offline wallet,” for example they are reputable brand such Ledger or Trezor like we providing on this site . While there are many different kinds of wallets, each has its own benefits, technical requirements and security. As with exchanges, you should investigate your storage choices before investing.
Diversify Your Investments
Diversification is a key to any good investment strategy, and it holds true when you’re investing in cryptocurrency too. Don’t put all of your money in Bitcoin, for example, just because that’s the name you know. There are thousands of options, and it’s best to spread your investment around to several currencies.
Prepare for Volatility
The cryptocurrency market is a volatile one, so be prepared for ups and downs. You’ll see dramatic swings in prices. If your investment portfolio or mental wellbeing can’t handle that, cryptocurrency might not be a wise choice for you.
Cryptocurrency is all the rage right now, but remember, it’s still in its infancy. Investing in something that’s new comes with challenges, so be prepared. If you plan to participate, do your research and invest conservatively to start.